While disinformation is getting a lot of attention in security circles, the discussion primarily tends to be in the context of election security. However, hacking social media accounts, or creating fake accounts, to post false messages about a company is absolutely a disinformation campaign.
External Author
Recent Posts
Disinformation Attacks Aren't Just Against Elections
By External Author on Aug 29, 2019 3:30:00 PM
1 min read
Tyler Robinson from Nisos interview during Black Hat 2019
By External Author on Aug 14, 2019 2:00:00 PM
While the industry as a whole must adopt a more focused and holistic approach to working together as offense and defense. Without a true devotion from red team offensive groups to truly help and work together with the blue team defensive groups we will never see a shift and maturity in security as a whole.
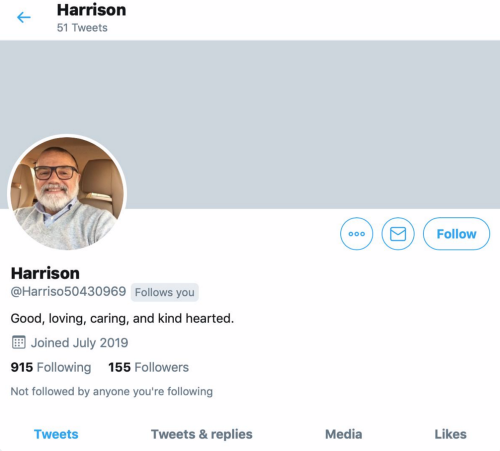
Spotting a Scam Account on Twitter
By External Author on Aug 14, 2019 2:00:00 PM
Meet Harrison. Harrison is “good, loving, caring, and kind hearted.” Harrison is also a fake account, though it might not look like it on first glance.
How To Control Your Digital Footprint Without Losing Your Mind
By External Author on Jul 25, 2019 12:30:00 PM
Note that this is not a one-time exercise, but a digital hygiene process which should be rinsed and repeated at regular intervals.
On The Fintech Carousel: Entering The Mobile Payments Space Requires Vision And Equilibrium
By External Author on Jul 11, 2019 1:00:00 PM
What lies ahead in fintech is a groundswell of rapidly and constantly developing regulatory requirements and unbridled opportunity.
Strengthening The ‘Soft Underbelly’ Of Cybersecurity (Part II)
By External Author on Jun 27, 2019 2:00:00 PM
Attack simulations, physical security, social engineering, and open source intelligence assessments can help law firms learn and self-correct before a real hacker gets through first.
Strengthening The ‘Soft Underbelly’ Of Cybersecurity (Part I)
By External Author on Jun 13, 2019 12:30:00 PM
Attack simulations, physical security, social engineering, and open source intelligence assessments can help law firms learn and self-correct before a real hacker gets through first.
Improving Organizational Collaboration In Response To Cyber Attacks
By External Author on Mar 7, 2019 3:00:00 PM
A comprehensive security management program gives equal weight to external and internal threats. While outsiders may know more about the latest attack methods, insiders have intimate knowledge about the company which can lead to loss of sensitive data and wreak havoc on profits and market share. By moving from a reactive, ad hoc strategy for handling insider threats to a proactive, preventative, and coordinated approach, companies can minimize the financial and reputational impact of insider attacks — and someday maybe even prevent them altogether.
Cyber Due Diligence Is Table Stakes for Effective M&A
By External Author on Mar 4, 2019 8:00:00 AM
The financial and organizational realities of two organizations merging or a smaller company being acquired by a larger one are profound. It’s critical to understand how to value, assess, protect and properly transition assets. Conducting thorough and reasoned cyber due diligence is an often overlooked but critical step in the cadence of M&A groundwork to a successful transaction.
Wickr's Top Lawyer Heads to Cybersecurity Startup as General Counsel
By External Author on Mar 1, 2019 12:00:00 PM
“Having spent five years at Wickr I was ready for a set of new challenges. It’s been really rewarding and fun to address a lot of the possible issues of the day in my role at Wickr,” DeTrani told Corporate Counsel. “But focusing on threats that exist within enterprises and how to help solve those threats is where I saw myself spending more time in the future. That’s why it made sense to transition to Nisos.”